Today’s hackers are using cyberattacks to target businesses of all sizes and steal sensitive data. These attacks are becoming more common and more sophisticated. Cyberattacks in Q1 2025 increased by 47% compared to Q1 2024.
To protect consumers from the fallout of these attacks, governments and industry regulatory bodies have implemented cybersecurity compliance standards. These standards require businesses to protect sensitive customer information with appropriate security controls to prevent data breaches.
Adhering to these regulations is necessary to avoid fines and legal action, but that’s not the only reason you should comply. A strong compliance strategy also protects your business operations from security risks, helping you avoid downtime and disruptions. Cybersecurity compliance is especially important for organizations operating in critical infrastructure sectors like healthcare, finance, and utilities, where breaches can have far-reaching consequences.
In this article, we’ll explore notable cybersecurity standards for businesses and provide actionable tips to help you implement a compliance strategy.
Key takeaways
- Organizations need to comply with location- and industry-specific regulations for consumer data protection, including HIPAA and PCI DSS.
- Failing to comply with these standards could result in fines, legal action, reputational damage, or even devastating cyberattacks.
- A strong compliance strategy includes technical safeguards, employee training, incident response plans, and regular audits.
Key cybersecurity compliance regulations and frameworks
Here are some of the most notable cybersecurity compliance standards for growing businesses to be aware of.
- HIPAA (Health Insurance Portability and Accountability Act): This law requires organizations to protect healthcare data and other personally identifiable information and limits how and when organizations can share this information. It applies to healthcare providers, insurers, and any other businesses that work with healthcare data.
- CCPA (California Consumer Privacy Act): If your business operates in California, you’ll need to adhere to this standard. It requires businesses to notify customers when they are collecting their data and give them the chance to opt out.
- GDPR (General Data Protection Regulation): This standard applies to organizations operating in the European Union. It gives consumers control over when and how they share their personal data, and requires businesses to protect the data they store.
- PCI DSS (Payment Card Industry Data Security Standard): This security standard applies to any organization worldwide that handles credit card data. It requires organizations to take appropriate security measures to keep cardholder data secure.
- ISO 27001: This international standard outlines best practices for information security management systems (ISMS). It helps organizations of all sizes secure their information assets by implementing a structured and risk-based approach to cybersecurity.
-
FTC GLBA Safeguards Rule: This regulation applies to financial institutions, including CPA firms, mortgage brokers, and investment advisors, even if they don’t directly handle money. Strengthened by the Federal Trade Commission (FTC), it requires these businesses to create and maintain a written information security program (WISP). Requirements include regular risk assessments, encryption, multi-factor authentication, vendor oversight, and assigning a qualified individual to manage the program. The goal is to protect customer data and reduce the risk of identity theft and data breaches.
Note that this is a non-exhaustive list. Your business may have additional regulations to comply with based on your industry and your location.
For example, many US states have their own data protection laws. California’s CCPA is considered the strongest, but states like Virginia, Colorado, Connecticut, and many others also have their own data protection laws with different security requirements.
Identifying your compliance obligations
When building your compliance strategy, you’ll need to determine which regulations and standards apply to your business. Consider factors like your industry, location, the number of customers you serve, and the types of data you collect.
Consider seeking legal counsel when building your compliance strategy to ensure that you don’t accidentally overlook any essential regulations. Research has found that 92% of organizations are not fully compliant with modern data privacy standards, but working with an expert can help you avoid falling behind.
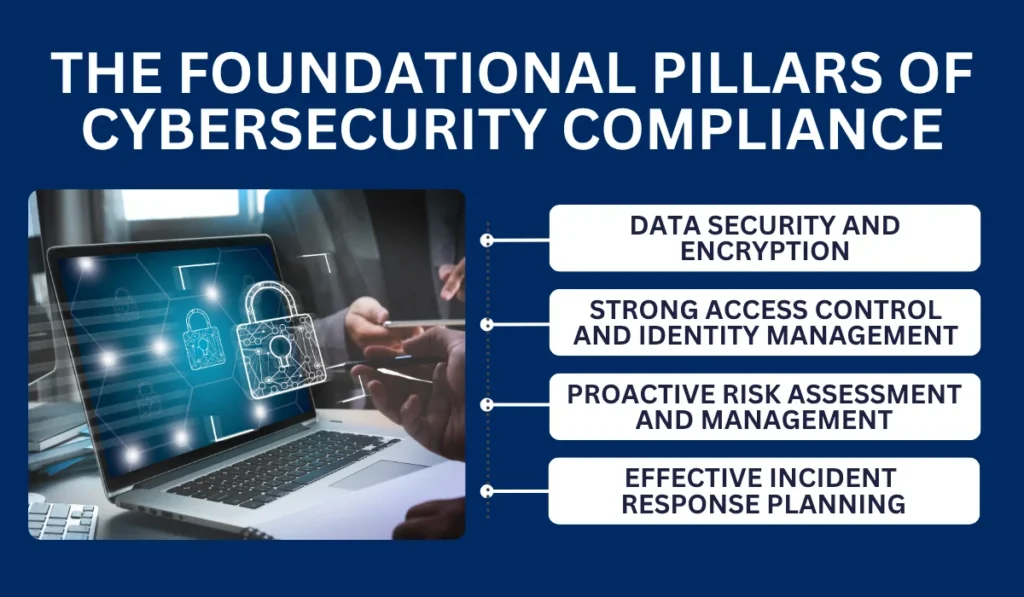
The foundational pillars of cybersecurity compliance
Most cybersecurity regulations are multifactorial, requiring businesses to take several different precautions to keep their systems safe. Here are the key components of cybersecurity compliance frameworks to be aware of.
Data security and encryption
One of the most important aspects of cybersecurity compliance is keeping personal data and other sensitive information safe from cyber threats.
This is usually done with encryption, which uses cryptography to obscure the contents of your digital files and communications. This way, even if hackers intercept your data, they won’t be able to read it.
Most cybersecurity frameworks require organizations to encrypt their data both in transit and at rest. When selecting data storage solutions and software platforms, look for providers that prioritize encryption.
Organizations should also practice data minimization, meaning that they only collect the minimum amount of customer data necessary for their operations. You should also practice secure data disposal when customer information is no longer needed, or when getting rid of old hardware programs.
Strong access control and identity management
Another essential component of cybersecurity compliance is limiting system access only to authorized users.
When granting system access, use the principle of least privilege, which only gives users access to the parts of your system they need to do their jobs. Your team’s access levels should be reviewed and adjusted regularly as roles change.
User accounts should be protected with strong passwords that cybercriminals can’t guess. You should also enable multi-factor authentication, which requires users to enter a third piece of identifying information to access their accounts.
Proactive risk assessment and management
Instead of waiting for cyberattacks to happen, organizations should proactively identify vulnerabilities and use risk management strategies to address them. Conduct regular audits to identify cybersecurity risks hidden in your systems.
This is essential for security compliance, but will also help protect your systems from potentially devastating data breaches. It’s easy to miss new cyber threats that emerge during your day-to-day operations, so conducting regular audits will ensure that you don’t fall behind.
Effective incident response planning
Even with a cybersecurity program in place, data breaches and other security incidents can still happen. Many cybersecurity compliance standards require organizations to respond to these incidents in a specific way.
For example, you might be required to notify customers about the data breach within a certain time frame. Some cybersecurity standards also require specific remediation efforts after a data breach.
Implementing and maintaining cybersecurity compliance: A step-by-step guide
Building a compliance program for the first time can feel daunting. Here’s a step-by-step breakdown to help you get started.
1. Understand your regulatory landscape
Not all regulatory requirements apply to all businesses. Start by taking a holistic look at your business and researching compliance standards that are relevant to your industry, location, and business operations.
Consider consulting with an information security compliance expert for extra guidance, especially if your business structure is complicated.
2. Conduct a comprehensive risk assessment
Next, perform a comprehensive audit of your entire system to identify areas where you’re at risk for non-compliance.
This audit should include all hardware and software, your network setup, your data storage practices, your information systems, and any other components of your cybersecurity posture. Flag any aspects of your system that could be compromised in a cyber attack and leave you vulnerable to regulatory action.
When conducting your audit, use cybersecurity frameworks and databases to guide you. For example, the NIST cybersecurity framework can help you systematically assess your systems and find new vulnerabilities you’re not already aware of.
3. Develop and enforce security policies
Next, develop comprehensive cybersecurity policies to guide your entire team in their day-to-day operations. These policies should cover access controls, encryption, and general security practices to reduce risks and maintain compliance standards.
For example, organizations that need to comply with HIPAA can implement policies specifying who is allowed to handle protected health information and how that information should be stored.
4. Implement technical safeguards
Most cybersecurity compliance standards require organizations to take reasonable steps to protect customer data. Adding technical safeguards to your system helps create a layer of defense against hackers.
This could include adding firewalls to your network, putting anti-virus and anti-malware programs on your devices, and using EDR tools to monitor for unusual activity.
5. Empower your employees through training
Phishing and social engineering attacks are significant threats to your business. These attacks rely on tricking your employees into revealing sensitive information, rather than launching technical attacks.
Provide regular training for your employees to help them spot phishing attacks in real time. Trained employees are often your first line of defense to prevent devastating attacks.
6. Establish and test your incident response plan
Create a robust incident response plan so your team can spring into action when a security incident happens. Test the plan with your team to address any challenges before a security incident happens.
7. Conduct regular security audits
Your compliance strategy should evolve as new threats emerge and cybersecurity restrictions change. Conduct audits at least once per year to identify new vulnerabilities and strengthen your security posture.
How managed IT services help you meet compliance requirements
For small businesses, working with a managed IT service provider (MSP) is often the easiest way to stay compliant and avoid data breaches. An MSP is a team of cybersecurity experts who can help with your IT and compliance needs, giving you more time to focus on running your business.
Your MSP will help you conduct thorough risk assessments and implement new technology and policies to stay compliant. They’ll also help with continuous monitoring and can help you recover quickly if you do experience a security incident. MSPs can also help with employee cybersecurity and compliance training, giving your entire team the knowledge they need to work safely online.
Cybersecurity compliance is an ongoing commitment and a central aspect of long-term business success. At Tech Advisors, we’re here to help with all of your IT and compliance needs. Get in touch with our team today to get started.